








Alibaba Cloud Security Center - The Eye of Horus
IT security management console
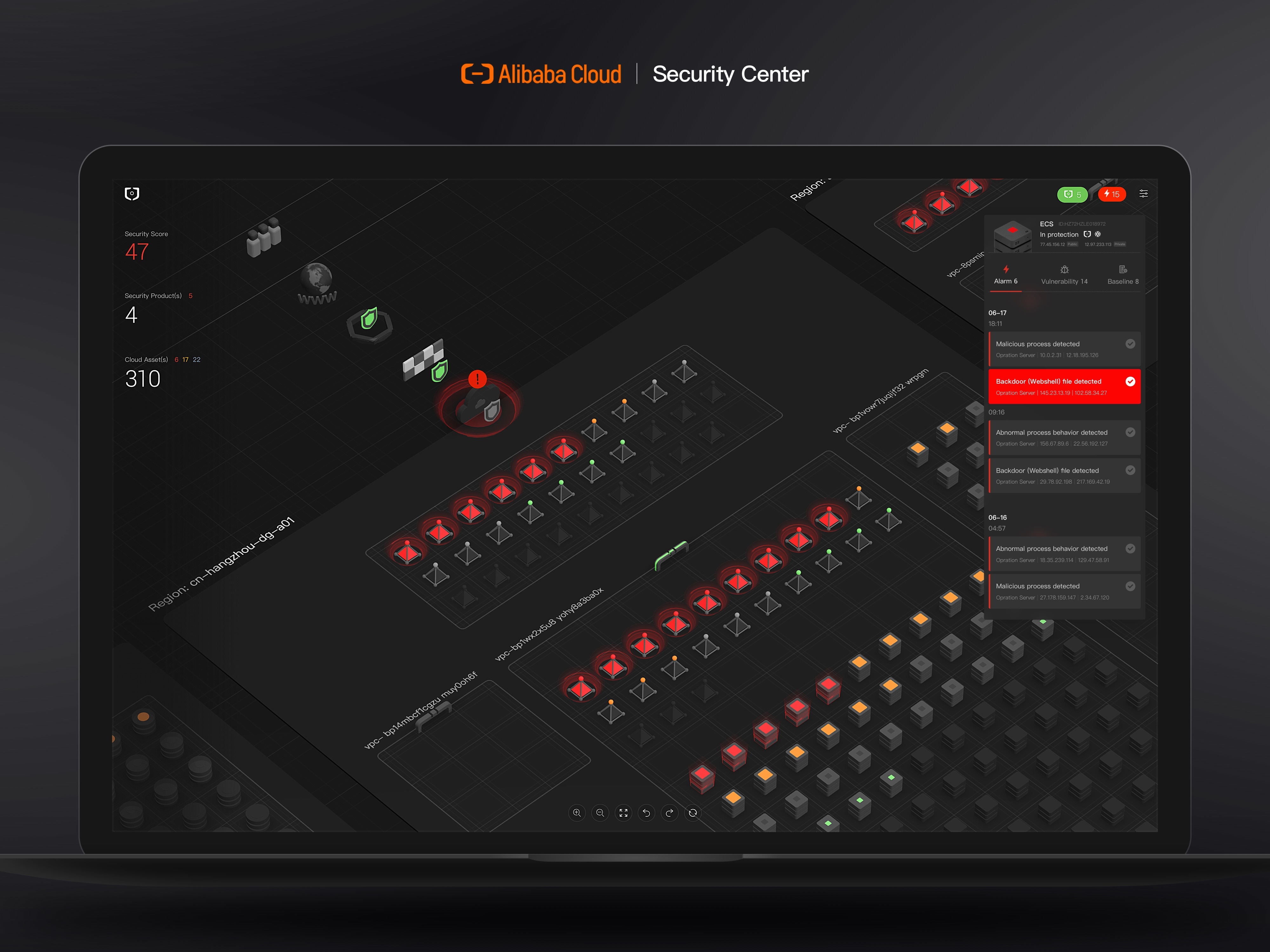
Alibaba Cloud Inc.Alibaba Cloud Security Center is designed for individuals and enterprises with zero to top IT skills to help them detect, analyze, and defend aginst cyber attacks from different locations and various levels of scale and complexity. The whole security management scene is visualized, from the user's real network topography, cloud assets, risk tracing, to cyber risk situational awareness. The developers took a design-centered approach, reducing the inherent security management complexity through 3D interaction and the back-end technology to empower users to adopt the best security strategy for their needs.
Date of Launch
2019
Development Time
up to 12 months
Target Regions
Asia, Australia / Oceania, Europe
Target Groups
Consumer / User, Trade / Industry, Public Sector Government, Other target groups: Mainly targets enterprises
